Trezor Login: The Gateway to Secure Crypto Management
In the ever-evolving world of cryptocurrencies, security should always be your top priority. That’s where Trezor steps in — a trusted hardware wallet designed to keep your digital assets safe from hackers and malware. But before you can enjoy the benefits of this robust security, you need to know how to navigate the Trezor login process effectively.
Why Use Trezor?
Trezor is one of the most popular hardware wallets in the crypto space, renowned for its user-friendly design and unmatched security features. Unlike online wallets that can be exposed to phishing or hacking attempts, Trezor stores your private keys offline. This “cold storage” method drastically reduces the risk of unauthorized access.
How to Login to Trezor
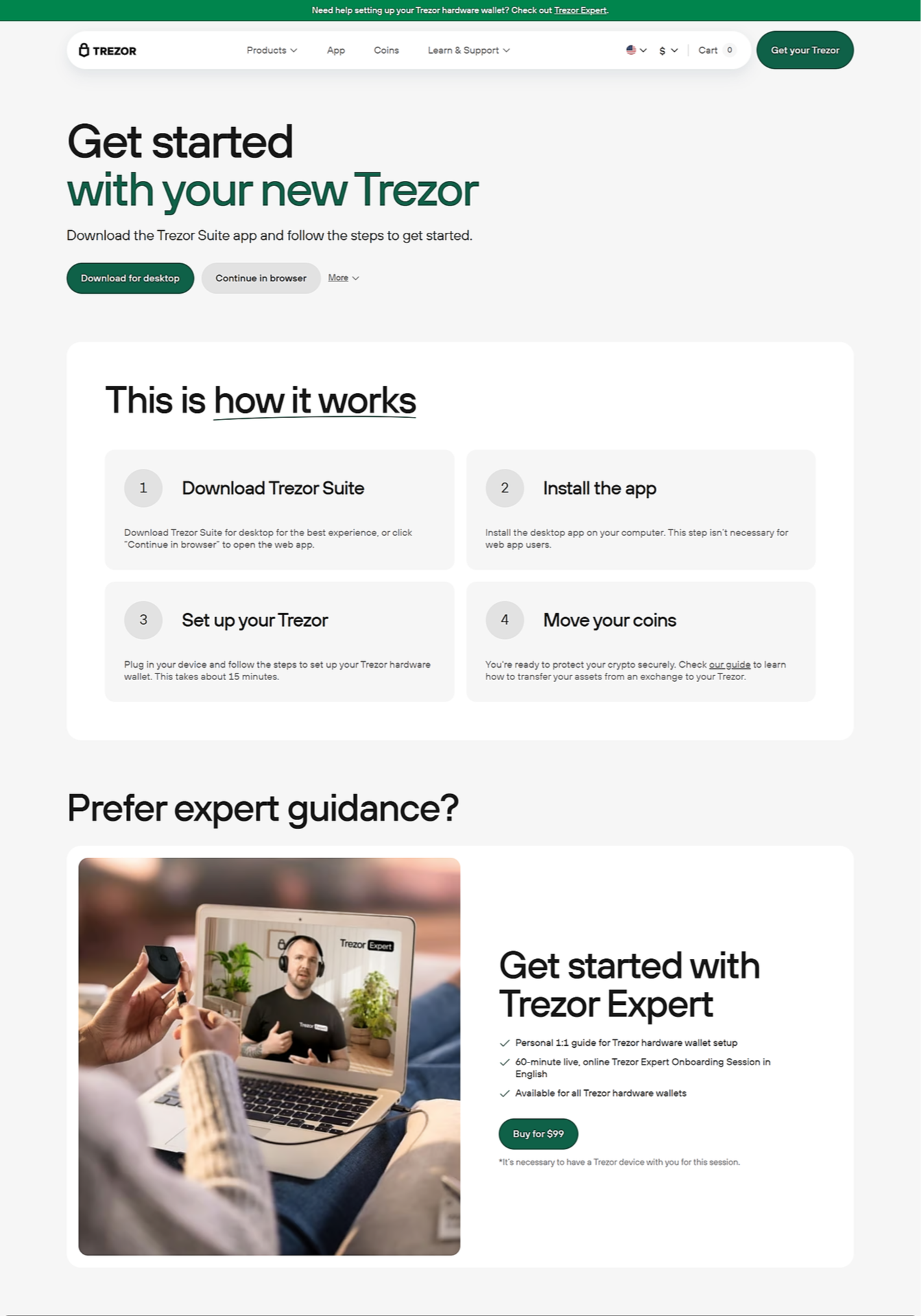
Logging in to your Trezor wallet is straightforward yet incredibly secure. Here’s how you can do it:
- Connect Your Trezor Device: Plug your Trezor wallet into your computer or mobile device using the USB cable.
- Open Trezor Suite: Visit the official Trezor Suite application or web interface. This is your command center for managing assets.
- Authenticate Yourself: Follow the on-screen instructions to enter your PIN directly on the device. This extra step ensures that even if your computer is compromised, your crypto stays protected.
- Access Your Wallet: Once authenticated, you’ll gain access to your dashboard where you can manage your cryptocurrencies, send and receive funds, and monitor your portfolio.
Advantages of Trezor Login
- Enhanced Security: Your private keys never leave the device, minimizing online threats.
- User-Friendly Interface: Even beginners can navigate Trezor Suite without hassle.
- Multi-Currency Support: Manage Bitcoin, Ethereum, and hundreds of other coins in one place.
- Recovery Options: Forgot your PIN? With your recovery seed, you can restore your funds safely.
- Open-Source Transparency: Trezor’s software is open-source, ensuring ongoing improvements and trust.
- Peace of Mind: Enjoy the freedom to manage your crypto without constant fear of cyber threats.
Final Thoughts
Mastering your Trezor login process is essential for keeping your digital assets secure. With Trezor, you’re not just storing crypto; you’re safeguarding your financial freedom. So, take a moment to ensure you’re logging in through the official platform and following best practices for ultimate protection. Your crypto journey deserves the best security, and Trezor makes it simple, safe, and stress-free.
Made in Typedream